Attack Surface Management
Uncover vulnerabilities before they're exploited. EASM meticulously scans and maps your digital footprint, identifying potential entry points for cyber threats. Gain a crystal-clear view of your attack surface, enabling proactive mitigation and reducing the chance of breaches.

Threat Intelligence
Real-time, actionable insights into emerging cyber threats, enabling proactive defense strategies. Stay steps ahead of hackers, safeguard your assets, and ensure uninterrupted business operations.

Fraud Protection
Discover, recognize, hinder harm, and safeguard against online deception. This includes methods to thwart both deceptive acts and the discovery of such acts. Fraud Protection services are employed to secure users online identities, halt automated bot actions, and stop fraudulent activities.

Digital Risk Protection
We keep a constant watch on domain names, databases for scams and phishing, ads, search outcomes, social media sites, and have specific tools to scan marketplaces, app stores, and messaging apps. We utilize words, patterns, and various ways to rank things.

Managed XDR
Detect dangers in real-time to facilitate instant response actions by gathering, connecting, and examining the extensive data produced by the different tools set up in your surroundings.

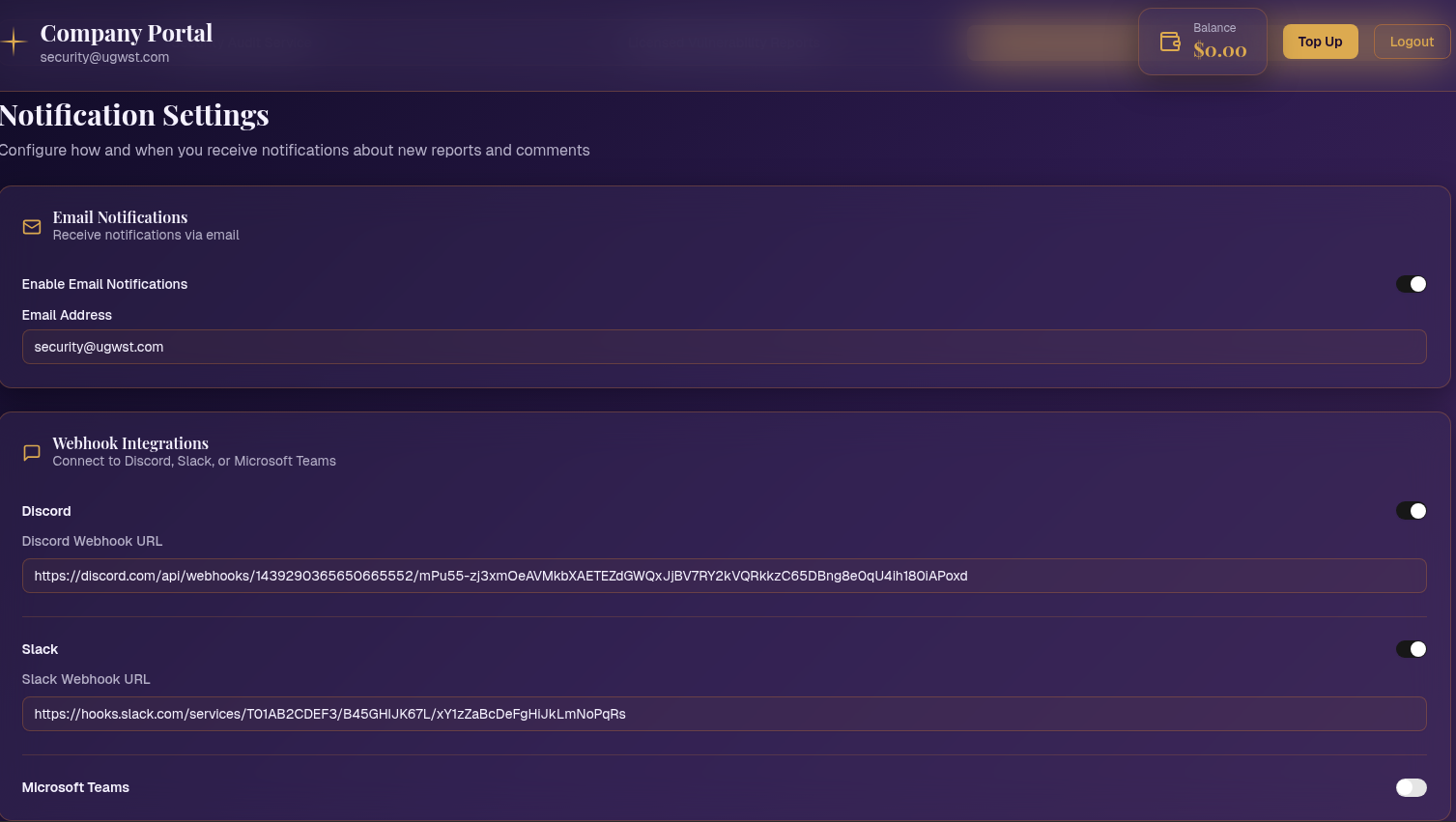
Business Email Protection
Easily keep an eye on your company's email security status using the customizable dashboard, or delve deeper into the specifics with more advanced analytics. Additionally, examine attachments and links, as well as analyze malware.

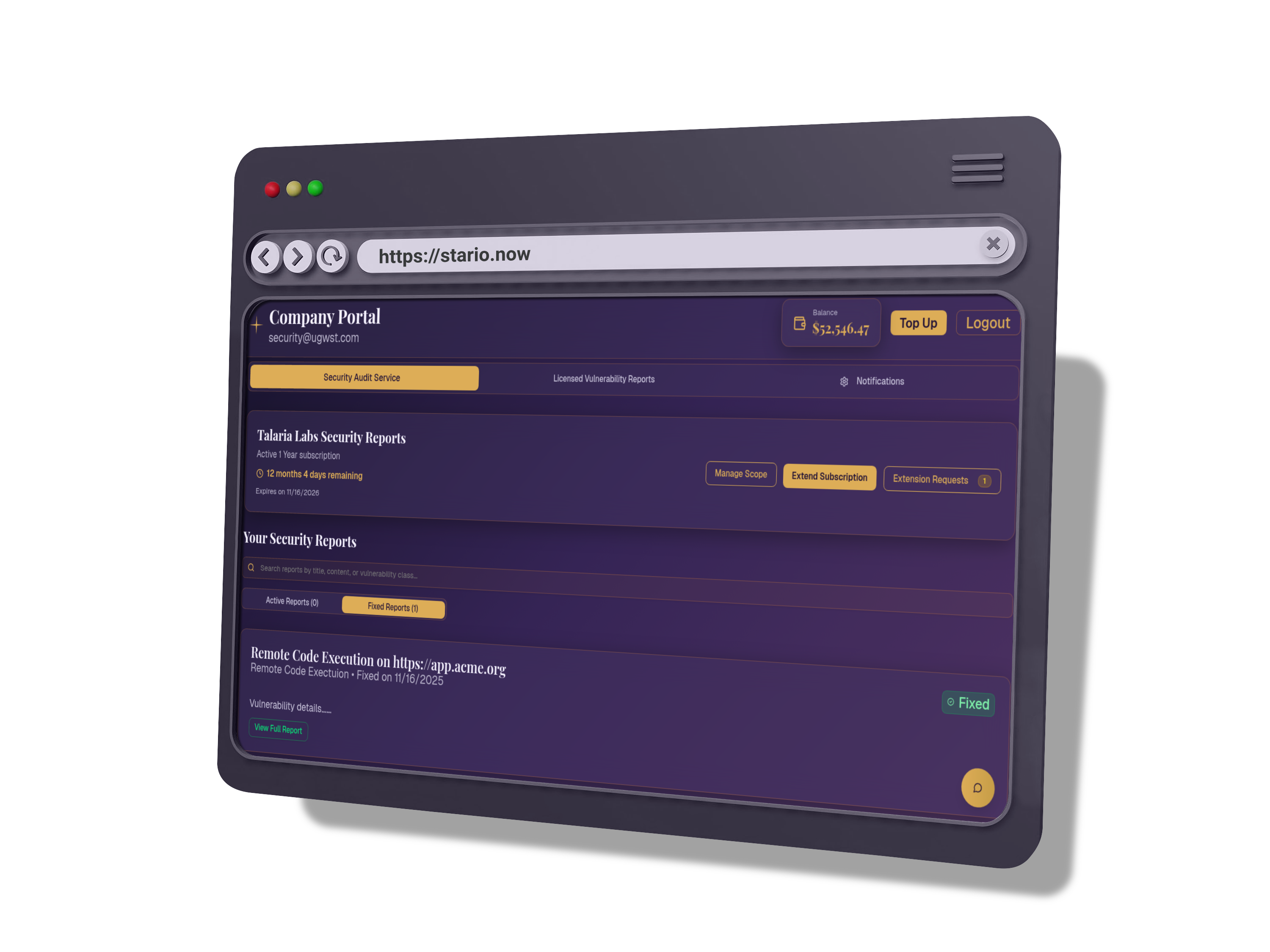
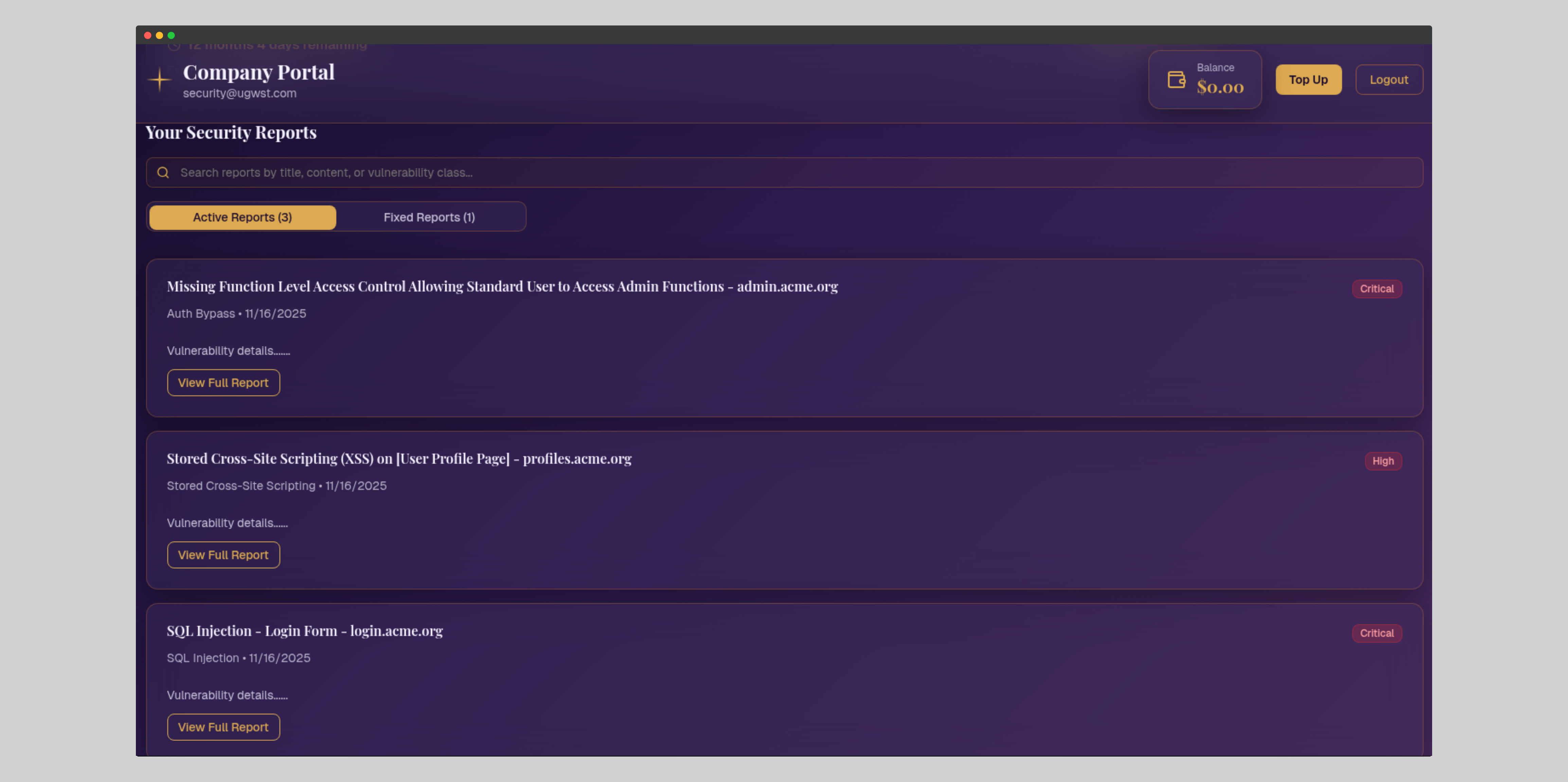
Bug Bounty Program Management
Talaria provides a full management service for the entire program lifecycle. This lets any company incorporate a Bug Bounty program into their existing vulnerability management procedures. They can use the same tools like ticketing systems and reporting mechanisms.

Cloud Security
Auditing security for cloud apps is distinct from regular checks. Third-party cloud systems usually have some security measures. Yet, various configurations in their consoles can create openings for breaches. At Talaria, we assess security by studying specific cloud components. We use tools and tests to find vulnerabilities.

Mobile App Assessment
App usage is rising daily, alongside frequent reports of new security vulnerabilities. To tackle this, our team will review apps per official standards. Our adaptable mobile app security check helps clients. We'll assess Android and iOS apps to spot and fix security problems endangering business and customer data.
Need more information or seeking alternatives? Contact us at [email protected]
%20(1)-p-500.png)