Fortune Favors the Vigilant
How We Saved a Customer from a KyberSwap-Like Hack

Introduction
In September 2022, the decentralized finance (DeFi) platform KyberSwap Network fell victim to a sophisticated hack that diverged from the conventional patterns of DeFi breaches. Unlike typical attacks on smart contracts, and web3 components, the threat actor exploited vulnerabilities within KyberSwap's frontend application, specifically targeting the website itself.
The attacker strategically injected malicious code into the platform's Google Tag Manager, a component part of Google Analytics Tools. This ingenious maneuver enabled the hacker to siphon approximately $265,000 in tokens from a single user's wallet.
This incident serves as a stark reminder of the evolving Web2 TTPs employed by threat actors in the DeFi landscape. In this article, we will describe how five months before the KyberSwap breach unfolded, our team at Talaria Security Labs (formerly known as UGWST) identified and intercepted a similar attack vector, saving a client from potential devastation.
Vulnerability Discovery
In May 2022, the security researchers at Talaria Security Labs were tasked to audit the front-end and web2 assets of a well-known large Web3 Project. For privacy concerns we will be referring to this project as AcmeWeb3 during this article. As per usual, our team started by identifying key areas of interest and high impact targets for the customer, which lead us to one of their main and most visited subdomains app.acmeweb3.io.
This subdomain was the main application used by customers and users to interact with most of the Web3 functionalities of the project such as borrow, send, receive, and exchange various funds. Therefore, a web vulnerability and attack on the website itself could potentially result in large financial and trust damages.
While looking at the technology stack used, and functionalities implemented by the app, the following line of code caught our attention:
<script type="text/javascript" src="/tracking-foobar.js"></script>
A closer look at the ``tracking-foobar.js`` source code revealed it to be an analytics tool similar to Google Analytics. Analytics tools like Google Analytics are utilized to track, analyze, and interpret user behavior and interactions on websites or applications, providing valuable insights and data that help businesses and website owners make informed decisions to enhance user experience, optimize content, and improve overall performance.
This was interesting to us because usually most projects and applications leverage the well known Google Analytics and Tag Manager. However, since this project seemed to be using a less known and “local” tool to gather analytics, we decided to investigate how this was implemented. These analytics tools essentially work by injecting JavaScript code into the website page, which will then handle the collection and delivery of data. This is important to highlight, since if one can control these tags and scripts, they can also inject any JavaScript directly into the front-end application without any user interaction required.
Upon inspecting at the source code, it revealed to be sending the analytics data to another endpoint: https[:]//app[.]acmeweb3[.]io/api/tracking-foobar/index.php?module=
After identifying which analytic technology was being used, our team began to research and read the documentation of the tool. Through the detailed public documentation, we were able to identify that in some instances it was possible to enable and use an “anonymous” login to interact with the Analytical Server holding the data. Although this was not enabled by default, we identified the customer had it enabled, and anyone could access several endpoints holding private data using this login.
Example Data Leakage 1:
Access to other websites: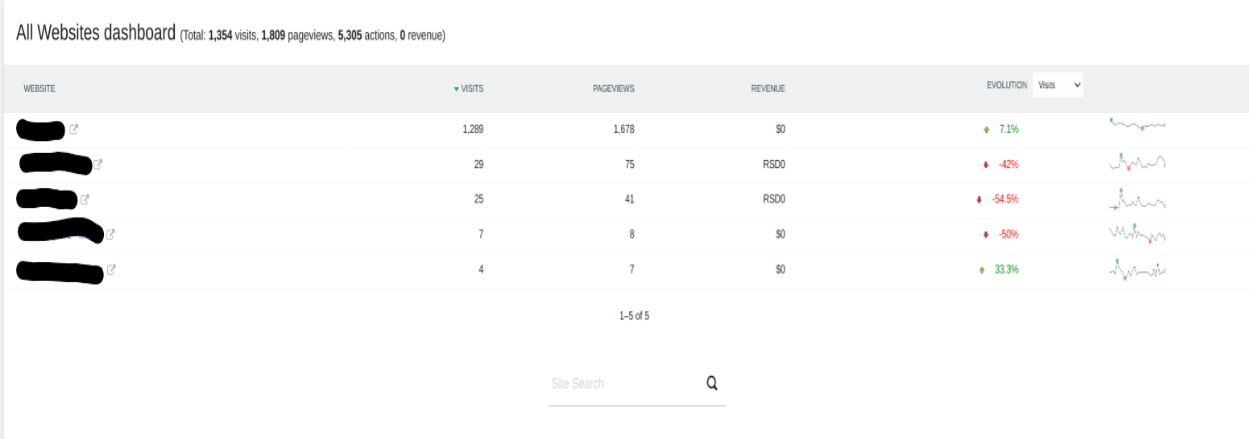
Although this is already a breach of user privacy, simply accessing web analytics data generally does not necessarily lead to critical impact to funds and users. However, as we continued to check all the available API calls and functions, we noticed that the anonymous login not only was enabled, but it was accidentally given super-user privileges. We were able to confirm this by leveraging High-Privileged API calls to create a new user, and give it admin access.
Creating user:
/api/tracking-foobar/index.php?module=API&method=UsersManager.addUser&format=html&token_auth=anonymous
&userLogin=talarialabs&password=NOTREALPASSWORD&[email protected]
Give New User Full Admin Access:
/api/tracking-foobar/index.php?module=API&method=UsersManager.UsersManager.getUsers&idSite=6&format=html
&token_auth=anonymous&access=admin&userLogin=talarialabs&idSites=1,2,3,4,5,6
Executing these API calls would give the threat actor an account with full access to not only the initial subdomain app.acmeweb3.io but also several websites that were also integrating the Analytics tool. Meaning that now, with admin access we were not only able to access and view all the data, but also modify tags being used in those sites and gain full stored JavaScript injection to several front-end applications.
Fortunately, our quick detection of the vulnerability allowed us to take immediate action, sparing our customer from the potentially devastating consequences of a real-world cyber attack. Our dedicated team worked seamlessly to provide detailed vulnerability insights, attack narratives, TTPs, mitigation strategies, and collaborated closely with the customer’s development team to implement robust security measures.
Key Takeaways
Frontend Vulnerabilities Pose Substantial Risks:
The KyberSwap incident and our experience with our customer underscores the critical importance of securing frontend applications in Web3 projects. Both cases reveal how threat actors strategically target vulnerabilities within the website itself, emphasizing the need for comprehensive security measures.
Proactive Auditing Mitigates Real-World Threats:
our customer’s proactive approach to seeking auditing services proved instrumental in preventing a potentially catastrophic hack. This highlights the proactive stance that Web3 projects can take to safeguard their platforms and assets by engaging in thorough security audits.
JavaScript Injection Exploits in Web3 DApps:
The KyberSwap incident highlights the severe impact of JavaScript Injection vulnerabilities in Web3 decentralized applications (dapps). A single compromised wallet led to the theft of over a quarter-million dollars. Understanding and mitigating these risks is paramount for Web3 projects to prevent similar financial losses and ensure the security of user funds.
Stay Proactive, Stay Safe
Ready to fortify your applications against potential threats and safeguard your users' assets? Talaria Security Labs specializes in comprehensive security audits tailored to the dynamic landscape of today’s modern threats.
Don't wait for a security breach to take action. Ensure the resilience and security of your organization and product by scheduling a consultation and security audit with us. Proactive security is the key to a robust and trustworthy application.
Reach out to us at [email protected] or visit our website at https://talarialabs.io to initiate the conversation and fortify your applications today. Your proactive steps now can save you from potential threats tomorrow.